Article 42
Study: Believing You’ve Slept Well, Even if You Haven’t, Improves Performance - Julie Beck - The Atlantic
Problem: Who even sleeps anymore? You and everyone you know are probably loading yourselves up with coffee or whatever your stimulant of choice is so you can plod through your day as some semblance of an upright human being. Then you get home and you don’t go to bed early enough because this is the only me-time you get, damn it, and if you want to watch three hours of Netflix, then you will. Or you try to go to sleep but you fail and end up tossing and turning, because sleeping is actually kind of hard, and the more you want it, the more it slips through your grasp.
But maybe the knowledge that you aren’t sleeping enough is part of what’s keeping you trapped in your swamp of lethargy during the day. Maybe if you were sweetly, blithely ignorant of your somnial failings, you’d feel more chipper and work more efficiently. In a recent study published in the Journal of Experimental Psychology, researchers from Colorado College tested the effects of being told you’re getting enough sleep—“placebo sleep,” as they call it.
Methodology: Participating undergrads first reported how deeply they’d slept the night before, on a scale of one to 10. The researchers then gave the participants a quick, five-minute lesson about sleep’s effect on cognitive function, telling them it was just background information for the study. During the lesson, they said that adults normally spend between 20 and 25 percent of their sleep time in REM sleep, and that getting less REM sleep than that tends to cause lower performance on learning tests. They also said that those who spend more than 25 percent of their sleep time in REM sleep usually perform better on such tests.
Then participants were hooked up to equipment that they were told would read their pulse, heartrate, and brainwave frequency, though it actually just measured their brainwave frequency. They were told that these measurements would allow the researchers to tell how much REM sleep they’d gotten the night before. This was not true.
Then one of the experimenters pretended to calculate that each participant got either 16.2 percent REM sleep or 28.7 percent REM sleep the previous evening. After getting their reading, participants took a test that measures “auditory attention and speed of processing, skills most affected by sleep deprivation,” according to the study.
A second experiment repeated these conditions, while controlling for experiment bias.
Results: Participants who were told they had above-average REM sleep performed better on the test, and those who were told their REM sleep was below average performed worse, even when researchers controlled for the subjects’ self-reported sleep quality.
Implications: A great victory was won here for lies, over truth. This study shows that if you’re in the mindset that you’re well-rested, your brain will perform better, regardless of the actual quality of your sleep. Conversely, constantly talking about how tired you are, as so often happens in our culture, might be detrimental to your performance.
The study, "Placebo Sleep Affects Cognitive Functioning," appears in the Journal of Experimental Psychology.
Stallman on GCC, LLVM, and copyleft [LWN.net]
Four Linux server monitoring tools | aarvik.dk
Comments:"Four Linux server monitoring tools | aarvik.dk"
URL:http://aarvik.dk/four-linux-server-monitoring-and-management-tools/
Here is four strong monitoring tools i would like to present for you.
htop - interactive process viewer
You may know the standard tool for watching real time processes on your machine top. If not, run $ top to see it in action, and $ man top to read the manual.
The htop is a widely extended version of top, with a big overview (eg. full commands, visualization, gui and ui), a mouse-clicking interaction, and a lot of guidance on how to do process management.
Install it and try it out: $ sudo apt-get install htop
Screenshot: 
- From my OS X terminal in my Debian 7 box
iotop - simple top-like I/O monitor
Iotop is a real-time monitor for IO. It displays information about each process thread in your system with their belonging detailed input and output (IO) usage.
This can be used together with $ tcpdump which respond with network traffic. If you can see that something is going on with your web server you can eg. check your port 80 (standard http port) networks traffics by running $ tcpdump port 80 to see details.
The most useful information is probably the DISK WRITE column, where you can see exactly how much process in K/s each IO uses.
Install it and try it out: $ sudo apt-get install iotop
Screenshot: 
apachetop - display real-time web server statistics
Apachetop displays a realtime table with http requests to your Apache webserver.
It displays stats, hits, requests, request details, and is good to get an overview for what is happening on your web server right now.
If you use Nginx there is similar tools, but seems like they are not as detailed as apachetop.
Install it and try it out: $ sudo apt-get install apachetop
Screenshot: 
Glances displays columns in separated tables for various useful real-time data about what is going on on your machine. Glances aims to show as much information as possible on a minimum of space, and i think it's goal is fully reached.
Glances monitor PerCPU, Load, Memory, Swap, Network, Disk i/O, Mount data and processes, with limited interaction possibilities and deep information, but is abosolutely perfect to get an big overview.
Install it and try it out: $ sudo apt-get install glances
Screenshot: 
Steve Jobs Unveils Mac at Boston Computer Society, Unseen Since 1984 | TIME.com
Comments:"Steve Jobs Unveils Mac at Boston Computer Society, Unseen Since 1984 | TIME.com"
URL:http://techland.time.com/2014/01/25/steve-jobs-mac/
It’s January, 1984. Steve Jobs, nattily attired in a double-breasted suit, is demonstrating Apple’s breakthrough personal computer, Macintosh, before a packed room. He speaks alarmingly of a future controlled by IBM, and shows a dystopian commercial based on that theme. He says that the Mac is “insanely great” and plucks the diminutive machine from a bag; it talks for itself. Screens of a graphical user interface — something few people had seen at the time — swoop by. The theme from Chariots of Fire swells. Jobs beams, as only he could.
This presentation, at Apple’s annual shareholder meeting on January 24, is the stuff of tech-history legend. What’s not so well remembered: Jobs did it all twice, in less than a week. Six days after unveiling the Mac at the Flint Center on the De Anza College campus near the company’s headquarters in Cupertino, Calif., he performed his show all over again at the monthly general meeting of the Boston Computer Society. His host, Jonathan Rotenberg, was a 20-year-old student at Brown University who’d co-founded the BCS in 1977 at the age of 13.
Over at YouTube, you can watch the Cupertino presentation, along with a sort of a rough draft held as part of an Apple sales meeting in Hawaii in the fall of 1983. As for the BCS version, all 90 minutes of it are there in the video at the top of this post, available for the first time in their entirety since they were shot on January 30, 1984.
The Cupertino and Boston demos may have been based in part on the same script, but the audience, atmosphere and bonus materials were different. In Cupertino, Jobs spoke before investors, towards the end of a meeting which also included dreary matters such as an analysis of Apple’s cash flow. In Boston, he presented to the kind of people who Apple hoped would buy Macs. You didn’t even have to pay the BCS’s $24 annual membership fee to get in, which meant that the meeting was the closest thing the computer had to a launch event intended for the general public.
People who attended the shareholder meeting saw the more historic presentation — hey, it came first — but what they got was also, in effect, a rehearsal for the later Boston one, which came out more polished. The BCS version was also longer and meatier. After the unveiling, Jobs participated in demos and a Q&A session with members of the Macintosh team: Bill Atkinson, Steve Capps, Owen Densmore, Andy Hertzfeld, Bruce Horn, Rony Sebok, Burrell Smith and Randy Wigginton. (Apple cofounder Steve Wozniak, not a Mac team member, crashed the panel and talked about the Apple II line of computers.) Even more than the shareholder meeting, the BCS one was a prototype for the media extravaganzas that we citizens of the 21st century call Stevenotes.
And I would have been there, if I hadn’t blown it. Though I had been a member of the club for five years and had already been eyewitness to history at its meetings, including demos of VisiCalc (the first spreadsheet) and the Lisa (Apple’s pricey proto-Mac), I didn’t attend the Mac event. What I was doing the night that Steve Jobs came to Boston I don’t remember, but I’ve been wincing about my misplaced priorities ever since. (I partially compensated a few years later when I attended the BCS meeting at which Jobs showed his NeXT computer; it remains the most dazzling tech demo I’ve ever witnessed in person.)
So many BCS meetings were so important that last year, I asked Jonathan — now a management consultant and executive coach — if any existed in video form. He referred me to Glenn Koenig, a Boston-area videographer who had recorded many of the proceedings. Glenn told me that he did have his vintage tapes — in storage, mostly on a now-obsolete format called U-matic.
Glenn also mentioned that Dan Bricklin might have more. Bricklin, the co-inventor of VisiCalc and co-founder of the company which produced it, Software Arts, had taped some meetings himself and then sponsored Koenig’s work. Back in the day, he had the foresight to realize that BCS meetings might be of lasting interest: “Saving these was important to me,” he says.
The matter slipped into the back of my mind until just recently, when I learned that my query had sparked Jonathan, Glenn and Dan to collaborate with Silicon Valley’s terrific Computer History Museum to digitize the videos of BCS meetings. Brad Feld, a venture capitalist who was a BCS member, gave generously to cover production costs and found others to chip in. (Bricklin has written about the preservation project and recorded a podcast interview with Jonathan.)
Jonathan’s team and the Computer History Museum graciously allowed the Mac meeting video to premiere here on TIME.com. (Excerpts were shown at the Mac@30 reunion event— held, appropriately, at the Flint Center in Cupertino — which took place on the night of January 25, 2014.) It’ll also be available shortly on the museum’s site, with more meeting videos to come, all available for free viewing. I’m not sure what I’m most looking forward to seeing: the meetings I attended decades ago, or the ones I missed.

A shaggy Steve Wozniak (in background) and Steve Jobs at the BCS’s Applefest ’82
One thing you need to know, assuming you didn’t happen to belong to the BCS in 1984: There was nothing the least bit odd about Steve Jobs showing up in Boston to court the members of a computer club run by a college student.
At the time, Jonathan was a noted industry educator/impresario, and it was pretty much a given that the East Coast premiere of any major new machine would happen before the BCS, which had thousands of members and dozens of special-interest groups. Apple was well acquainted with the organization, having shown off multiple earlier models at its meetings; both Jobs and Wozniak had attended Applefest, a BCS-produced shindig for Apple II users, in 1982.
In November of 1983, Apple flew Jonathan to its Cupertino campus, where he got a briefing on the Macintosh and began work on a 16-page review of the computer for the BCS’s slick bimonthly magazine. Plans began for the Mac meeting, to be held at New England Life Hall, the site of the BCS’s general meetings.
And then they almost fell apart. The Flint Center’s 2,600-person seating capacity turned out to be far too small for the crowd that showed up on January 24. “More than a thousand shareholders were not able to get in, and weren’t able to participate in shareholder voting and discussion,” Jonathan says. “They were really angry about that.” The PR crisis was so severe that the video of the meeting the company produced at the time opens with an abject apology by CEO John Sculley.
Jobs — as you already know if you know anything at all about Steve Jobs — was apoplectic over the botched crowd control. “The next day,” Jonathan says, “Steve Jobs said ‘We’re canceling Boston. We don’t want a repeat of all those people waiting outside and not being able to get in.’ This was now five days before the event.”
Miraculously, the BCS was able to secure a more spacious venue for the night of the meeting: John Hancock Hall. It had a room in which any overflow crowd could watch a video feed, and space for banks of Macs for hands-on demos. “After very, very tense negotiations, Steve finally relented and agreed to come to Boston,” Jonathan remembers.
“Ironically, his worst fear came true: There were more than 600 BCS members stuck outside who couldn’t get in. But at least they weren’t Apple shareholders.”
Fortunately for posterity, the production values on the video version of the meeting are quite good — far better than what Apple managed for the shareholder meeting. (In Cupertino, the lighting had been so murky at times that the only thing you can see clearly is Jobs’ white shirt gleaming from inside his jacket.) Apple sprung for multiple cameras, one of which was manned by the BCS’s Koenig. Moments with subpar camera work in the Cupertino video, such as when Jobs pulls the Mac out of its bag and boots it up, are nicely shot in this one.
As presented here, the video — which is a rough cut of the version that the Computer History Museum will preserve — has a few moments that have been reconstructed. The slides Jobs shows are the same ones he presented in Boston, but they’re borrowed from the video of the Cupertino event. And when Jobs shows a blurry slide of the IBM PC — provoking mirth from the audience and prompting him to say “Let’s be fair” — the blurring is a recreation of what really happened. (To this day, Rotenberg isn’t sure whether it was a prank on Apple’s part or a bona-fide technical glitch.)
“It’s so much more intimate,” Rotenberg says of the Boston version of the presentation. “It’s about the users, which is what you don’t get at the shareholder meeting.”
“This one was Steve really selling,” says Bricklin, who has shown clips of the presentation in talks to students for years, in the only instances of it being seen in public since it was recorded. “This is the Steve that we’ve now known for many years announcing other products. This is that Steve, giving the talk he’s given so many times that he knows it cold. It really makes a difference.”
“You get to see Steve when Steve became the Steve Jobs. Seeing him smiling up there is the way a lot of us would like to remember him.”
Though the first portion of the BCS video follows the same script as the Cupertino event, Jobs keeps going after first version concluded — and what he says is some of the most classic Jobs I’ve ever seen. Adopting a simile he later used in a 1985 Playboy interview, he compares text-oriented computers such as the IBM PC to telegraph machines, and the Mac to the telephone:
Now, if you go back about a hundred years, to the 1880s, there were approximately twenty, twenty-five thousand trained telegraph operators in the United States. And you really could send a telegram between Boston and San Francisco, and it’d take about three or four hours and go through the relay stations. It really worked. And it was a great breakthrough in technology that had been around for about thirty or forty years. And there were some people that talked about putting a telegraph machine on every desk in America to improve productivity. Now what those people didn’t know was that about the same time, Alexander Graham Bell filed the original patents for the telephone — a breakthrough in technology. Because putting a telegraph on every desk in America to improve technology wouldn’t have worked. People wouldn’t have spent the twenty to forty to a hundred hours to learn Morse code. They just wouldn’t have done it. But with the telephone, within ten years there were over 200,000 telephones on desks in America. It was a breakthrough, because people already knew how to use it. It performed the same basic function, but radical ease of use. And in addition to just letting you type in the words or click in the words, it let you sing. It let you intone your sentences to really get your meaning across. We are at that juncture in our industry right now. There are people suggesting that we should put a current generation box on everyone’s desk to improve productivity. A telegraph, if you will. And we don’t believe that. We don’t think it’ll work. People will not read those damn 400-page WordStar manuals. They won’t carry around these cards in their pockets with 150 slash-W-Zs. They’re not going to do it. And what we think we have here is the first telephone. And in addition to letting you do the old spreadsheets and word processing, it lets you sing. It lets you make pictures. It lets you make diagrams where you cut them and past them into your documents. It lets you put that sentence in Bold Helvetica or Old English, if that’s the way you want to express yourself.What Jobs said reminds us that the Mac’s competition was less other computers of the time than it was no computer at all. It’s a hyper-dramatic, self-serving way to look at how the Mac compared to everything else available in January of 1984. But hindsight — and the fact that every other PC maker ended up following the Mac’s lead — confirms that he was right.
The audience is enthusiastic during Jobs’ splashy presentation, but it’s far more giddy during the live demos of Mac apps that follow. That didn’t surprise me: BCS members prided themselves on being discerning, demanding consumers, not gearheads or fanboys. Real software impressed them more than mere hoopla, and programs such as MacPaint and MacWrite were knockouts. When Atkinson pastes a sphere in MacPaint multiple times, there’s sustained applause — yes, cutting and pasting was impressive at the time — and he breaks out in a grin that’s a joy to behold.
“It was wonderful that he actually brought the team to share and bask in the glory — they weren’t there for the shareholders’ [meeting],” says Bricklin, who doesn’t see much difference between the flavor of their camaraderie and collaboration and what goes on today at a company such as Google or Facebook.
The questions from the audience neatly capture the most pressing questions that the computer users of 1984 had about Apple’s new machine. They ask about plans for more memory and disk expansion; how MacWrite compares to the era’s dominant word processor, WordStar; what programming tools will be available; what’s next for Apple’s best-selling computer of the time, the Apple IIe. Someone even asks about the fate of the already-moribund Apple III. (Jobs: “I wouldn’t have called on you if I’d known that was your question.”)
Then there’s the audience member who asks if the Mac can do animation. Jobs — in this pre-Pixar era — seems slightly taken aback by the subject, and hands the inquiry over to Andy Hertzfeld.
As Jobs answers other questions, he neatly ticks off most of the developments that kept Apple busy until the early 1990s. He talks about hard disks (then often called “Winchesters”), laser printers, color graphics and even the portable computers (“a Mac in a book”) the company will someday build. Today’s Apple may be famously close-mouthed about unreleased products, but back then, it had to assure skeptical buyers that its just-born platform had a future.
After the panel discussion, Jobs thanks the audience and pays tribute to the team. (“When you use a Macintosh, these are the people that did it. And they’re sort of hiding out in that ROM.”) In the video, you can see some attendees heading for the exits as the lights come up. It wasn’t supposed to be that way. Jobs was supposed to introduce Jonathan, who, in the BCS meetings’ standard format, would normally have introduced Jobs but had agreed to flip the order. “I was pretty miffed,” says Jonathan. As he arrives onstage in the video, he makes a snarky reference to Big Brother controlling the audio-visual system, riffing on the “1984″ commercial.
Don’t make the same mistake as those 1984 audience members and tune out after Jobs finishes. Jonathan’s concluding remarks include mention of “insanely great” upcoming BCS meetings, including one featuring IBM’s famously bad PC Jr. — which, as you can tell from the snorts from the audience, was already a punchline — and another in which Atari cofounder Nolan Bushnell will demonstrate his new startup’s robots. He also announces that the BCS is starting what may be the world’s first Mac user group.
It’s an evocative little snapshot of where technology was in early 1984, and you get to see enough of Jonathan at work to get a sense of why he was both respected and beloved by BCS members in particular and the industry in general.
Keep watching even after Jonathan wraps up. The very end of the video includes footage of attendees trying out Macs for themselves, plus snippets of them grilling Wozniak, Sebok, Hertzfeld and Capps with even more questions.
What are Rotenberg’s thoughts upon seeing Jobs, and himself, at the event after 30 years? He says it leaves him nostalgic for the era when personal computers were new. The BCS played an important role in demystifying them, and anything and everything seemed possible.
“It’s a time of life I feel a tremendous connection and affection for,” he says. “I think of what people talk about with the 60s or the Camelot era with JFK. It was an amazing time to be alive, and to be part of something. But there’s also a sadness that it’s gone.” (The BCS itself disbanded in 1996, at least in part because computers no longer required as much demystification as they once needed; I was dismayed to hear the news even though I’d let my own membership lapse.)
In September of 1985, Jobs was forced out of Apple. Jonathan went on to graduate from Brown, dial back his role in managing the BCS and enter Harvard Business School. The high of the Mac’s debut felt like part of the distant past. “All of these cottage industries got consolidated or run over by the next generation of companies, like Dell,” Jonathan says, still sounding pained by the memory.
“By the time I got to business school, Steve Jobs had become a model of inept business management. In ‘Introduction to Marketing,’ on the very first day, the example of how to do everything wrong was the Macintosh. It was held out as making a product based on some dreamy-eyed guy’s personal whims, with no relation to what the market or customers want.”
“That kind of thinking became vilified as the cause of why so many smaller companies had crashed in the technology world, and why you wanted big, capable companies like Digital Equipment and IBM and Xerox to lead the way. Everything that Steve Jobs had done that resonated so personally with me was like this disease that had to be destroyed.”

Members of the team that created the Mac — including several who participated in the 1984 BCS meeting — reunite onstage during the Mac@30 event at the Flint Center in Cupertino, Calif. on January 25, 2014
It was pretty depressing. But we now know that it wasn’t the end of the story.
In 1996, Jobs sold NeXT to Apple and began his second act at Apple. In the years that followed, Apple once again took on the clunky telegraph machines other companies manufactured with elegant, approachable telephones. (With the arrival of the iPhone in 2007, the part about the company’s products being telephones stopped being a metaphor.) And when Jobs was studied in business schools, it wasn’t for being a dreamy-eyed failure.
“As he got his momentum going, what was so powerful to me was just observing how we’d had a period of eleven years when Steve Jobs was in exile and we could see what was happening to the PC in that time,” says Rotenberg. After Jobs returned, “what he made possible left no doubt in my mind that a single person really could change the world.”
Teapotnet
Comments:"Teapotnet"
zyalt: Revolution in Kiev, Ukraine
Comments:"zyalt: Revolution in Kiev, Ukraine"
URL:http://zyalt.livejournal.com/984735.html
Sharing and distribution is appreciated.
22 January 2014. Battles on streets of Kiev.
I came to Kiev. I came to see for myself what is happening here. Of course, an hour after arriving at Maidan, you begin to understand that everything what you've read in dozens of articles, saw in TV news reports is total crap. In the upcoming reports I will try to, as objectively as possible, to sort out this new wave of Kiev revolution.
Usually reporters try to answer the question: “Who came out to Maidan and why.” Depending on the political leaning of MSM, the answers are different. Some say it's “fascists who came out to lynch the Moscali (Ukranian derogatory for Moscovites and Russians in general).”, some say “they're bums and slackers, who've got nothing better to do” and “instigators on the government payroll.” In reality, there is no answer. Those who came out are completely different. Remember, how a couple of years in Moscow there was a MSM buzzword “angry townspeople.” Here you see football fans, retirees, office plankton. And everyone is standing together. A sweet, ol' grandmother is pouring Molotv cocktail in a nationalists' bottles; and a manager of a large company is carrying ammunition to the student. And as it seems to me at this time, these people do not have a specific plan, nor idea of what to do next. Of course, individually, everyone has their own plan to “save Ukraine.” For some its “we need a couple of crates of AKs and grenades, we'll sort things out here quickly.” Others “need to ask the world community for help and bring in the UN troops.” At this time there is no central idea of what to do, an idea that can unite and point in one direction the people at Maidan.
The only thing that is completely clear – people came out against Yanukovich.
The burning barricades are visited by people who have come to let out anger and resentment that have accumulated over the years – for the excesses of cops; for the corruption; for the 'golden toilet'; for the stupidity of the sell-out officials. An elderly man, 80 years of age, walks up to young guys in masks and asks them for a bottle of flaming liquid. They ask him:
“- Grandad, you wont be able to throw it far enough!
- Just give me one, I want to show these beasts that they cannot treat me like this”
Unfortunately, the Ukranians had bad luck with opposition. The street mob is not controlled by anyone. Klichko and his company met with Yanukovch yesterday. Later they came out to the people, began to say something, but no one believes them. And no one wants to follow them. The main mass of people are completely non-political. They come out to kick Yanukovich and his company's ass. Everyone has their own grievances and vision of the future.
There are very real battles on the streets of Kiev right now. Unfortunately, Yanukovich is far, so the Berkut (Ukranian SWAT) and soldiers have to play the role of Yanukovich' ass. The scenery in Kiev is scary. Black smoke, burning barricades and constant explosions. Berkut's flashbangs and the protestors' fireworks explode in the streets. Each side is shooting at the other and there are already first casualties(2 to 5 based on different sources).
Let's go to the barricades?
I rented a room in the hotel "Dnepr", the very center on the European square. I come up to the main entrance, all doors are locked, lights are out. A group of men in helmets and protection, hanging nearby, greet me “Welcome to Kiev, Mister.” - they've confused me with a foreign tourist. Everyone's laughing. It turns out that the entrance to the hotel is through a local bar. The security guy opens the door and leads me through dark hallways to the lobby. The lights are off, so as not to attract attention. After all, the hotel is almost at the front line.
1. European square. Back when it was all starting, there was a stage here, from which politicians pontificated their smart ideas about the future of Ukraine. Now the politicians have move on to Maidan, and the European square has become the rear base of the revolution. Cars with food arrive here; old tires for the bonfires, wood, medicine and reinforcements.
2. Mihaila Grushevskogo street. The first barricade has been erected here. The guards do not allow in outsiders. Only the press, the volunteers, and the activists, ready to fight Berkut, are allowed to pass. All onlookers are stopped at the approach, to prevent them from interfering with work.
3. This is main burning barricade near the Dinamo stadium, about 100 meters away from the first. It consists of hundreds of burning tires, which are brought here from all parts of the city. The demonstrators got lucky with the wind – it carries the black smoke directly at the squads of Berkut and national guard standing behind the fires. The smoke completely obscures the view and both sides are currently working blind.
4. A bunch of onlookers watch the fight. The battle continues for 4 days in a row.
5.
6. Activists run up, bearing shields and toss stones. Nobody sees the enemy, but everyone knows how far Berkut can toss grenades. No one approaches the determined line without a shield. The grenades that land are flashbangs and tear gas. This does not have much effect on the seasoned protestor. The key is to avoid a direct hit or a nearby explosion, which can cause concussion.
7. The fire is constantly fed by more tires. The smoke screen must be dense! At one point Berkut attempt to feel out the protestors from a hill using a powerful projector.
8.
9. There are special men on the field of battle, who watch the troop movements of the opponent. The man in the mask and shield will always tell you where it's safe: “Stop! There's a devil shooting from behind the column, don’t go father that line! We're about to smoke him out of there!”
10. The scouts constantly refresh information about the enemy position and coordinate activists, who toss stones and Molotov cocktails.
11. The authorities turned several water cannons at the demonstrators. Surprisingly no one is afraid of the water. This scout is climbing a balcony to see what's behind the smoke screen. The drenched people dry at the campfires. And some just walk around wet. There's an incredible atmosphere here: on one hand you can feel the weariness of the frustrated people, on the other hand euphoria and expectation of victory. In such light, no one is paying attention to wet clothes. Only medic volunteers ask people to go warm up to avoid frostbite.
12. Activists with Molotov cocktails at the front line.
13.
14. Actually the center of Kiev is very pretty right now
15. Protestors periodically shoot fireworks at Berkut. The entire square lights up and people cheer.
16. Somewhere over the the Berkut troops are getting ready for another assault. The assault is always sudden and everyone fear its. This morning Berkut has already shown that if the need be they can scatter everyone in 5 minutes. Why they do not – is a different question.
17. Catapult 1, seized and destroyed, is replaced by Catapult – 2. In reality it's just a large slingshot, but to keep continuity the call it Catapult – 2.
18. Miracle of the engineering thought! Catapult -2 quickly went through testing and was admitted into the armament of the rebels. The crew consists of six people: three people pull the elastic; two people hold the frame; one person loads and delivers ammunition.
19. The wonder machine works well, but slow. The missiles fly far into the night, but reloading takes 2-3 minutes.
20. In a nearby alley people prepare Molotov cocktails. In reality, most of the bottles contain either pure kerosine or gasoline, the recipe is no longer followed – no time. Empty glass bottles are in a big deficit.
21. I'm looking at the guys and everyone is drinking Pepsi. I'm wondering: why drink this crap, it's freezing outside? As it turns out, bottles ran out and someone brought several crates of soda. So as not to waste, everyone's drinking together. Even infant food jars are used. All glass containers fly at the cops. The filling of the containers at the front line is done by the activists of the 'right sector,' but in the rear the bottles are filled by regular grandmas and pretty young women. Those who the guards do not allow passage to the front.
22. There are problems with bottles here. The mixture inside is liquid, not thick like in the original Molotov recipe, and the fuse is a simple rag. During the throw part of the gasoline can spill out and light up the thrower. Of course the fire is quickly put out, but the effect is very low. Almost 50% of all cocktails spill out before hitting their target.
23.
24. The onlookers on the hill help out in any way they can. Sometimes they use lasers to blind the Berkut fighters. At one point the police was able to climb the colonnade entrance of the stadium and began to rain Molotovs and gas grenades down on the protestors. The onlookers use lasers to hit a Berkut in the eye, or try to find snipers on the roofs. There are constant rumors of snipers, although no confirmation of their existence has been produced. 
25. Volunteer giving out dry, waterproof boots at the front line.
26. A young woman with a tea kettle approaches an activist on the front line to keep them hydrated. Some carry sandwiches, some dry clothing. Later I will describe in detail how things work here.
27. Campfire behind the barricades, where the wet and the frozen dry and warm up.
28.
29. On my way back I see a group of people, trying to open a manhole. I ask them why are they trying to open the manhole? “We want to turn off the water so that Berkut will stop hitting us with water.!” The manhole does not open, this is a government district and all manhole covers are sealed securely from inside. Later they tried to break the manhole cover with sledge. I tried to explain that this is pointless, but I was ignored. The were not able to break through and they're still getting hit with water.
23 January 2014. Temporary cease fire at Maidan.
30. 
I would like to dispel the most common myths about Maidan.
1."They destroyed the whole city"
Not true. All of the action you see in the pictures are happening on a small square near the entrance to a Dinamo stadium. This is a government sector, there is no intereference in peaceful life outside of this area. If you make an analogy with Moscow, imagine that the barricades are someone in the area of Ilinka or Varvarka, near the president's administration. Sure, it's the center, but regular Moscovites wouldn't notice. There is dark smoke and fire on all pictures: those are mostly burning tires. There is not tangible damage to the buildings. Unfortunately one store burned down last night near the barricades, resulted from a poorly thrown molotov cocktail. Even the statue of Lobanovsky, located in the epicenter of fighting has been covered with cloth to prevent damage. Overall, the protesters are very careful regarding property. They've take apart fences and benches, but no windows are broken, noone is vandalizing, and all looters are caught and beaten. So the picture is pretty apocalyptic, but things are not so bad.
2. "This is not a revolution, nothing horrible is happeneing"
Also not true. This is a real revolution. Decide for yourselves: it's been two months since the center of Kiev has been in the hands of the opposition. Several government buildings are seized. The work of many government offices is paralyzed. The opposition has created barricades, which the authorities have not be able to take. Despite the freezing temps, tens of thousands of people are on the streets for the last two months. The system of defense and supply chain are established. There is perfect order at the protestor HQ, people are fed, dressed, people are pooling money to gather supplies. The most important thing: the people in power are unable to restore order. The police has failed several times at try to storm the barricades. I'll make a separate post about this, but trust me, the only way to dismantle this is with heavy artillery, or drop in commandos. Every day the opposition is securing more territories. What is this if not a revolution?
3. "The entire Kiev is paralyzed, there is no peaceful life for the regular people."
Kiev is living its own life. All stores and cafes are working, people are going to work, study in universities, get married, divorce and even die their own death. Most of the Kiev populace are not inconvenienced. Imagine if Navalny took over the Red Square and set up his camp there. What would change for you, Moscovites? Nothing. So the only people who are inconvenienced are toruists. A few stores and cafes had to close down in the very center. Also, those living in the center have troubles with logistics. But the entire Kiev is not paralyzed.
Now, when you know all the truth, let’s see how this day was.
31. From the morning everything remains in fire.
32. The protestors use metal shields to defend themselves from water the police are pouring them with. 
33. Road signs can serve as good shields.
34. The Maidan’s missile forces. Lots of pyrotechnics are being brought up to the camp, all these rockets fly towards Berkut’s positions.
35. Hearths always require more tires to be thrown into. Because of ash and ice, ground level already rose by one meter.
36.
37. Where necessary, the police gets stoned.
38. Everything is tightened with a smokescreen. Burning tires turned out to be a very efficient tactics. Police troops can’t see what is happening and are unable to attack, though there are disadvantages as neither the protesters can see the police’s positions. 
39. This night was burned children’s clothing store.
40. A catapult is always working on the front line.
41. Not many people show up on the Maidan in the morning – the majority arrives at night, after work.
42. 
43. At midday Klichko came to the barricades and announced the temporary truce. Second round of negotiations with Yanukovich was due to take place today, and Klichko asked to cease fire and extinguish tire blazes until 8 PM. The police promised not to open fire on protesters, to stop throwing grenades and pouring water. Everyone agreed – Klichko happened to be the only opposition leader whom the crowd listens to. Well done! Just yesterday nobody was listening to him. After the truce came into effect, firemen started extinguishing the burning barricade.
44. A wonderful view opened once the fire went out.
45. People immediately started advancing to the forefront which was previously engulfed by fire.
46. Berkut’s positions.
47. Berkut troops were standing angry and soaked in smoke. Throughout the truce I spotted no provocations from either side.
48. Protestors are making photos in front of Berkut, Berkut in front of the protestors – war is war, but everyone needs to updates pics in social networks.
49.
50. Scores of soldiers and Berkut are standing in small groups up to the horizon. 
51. 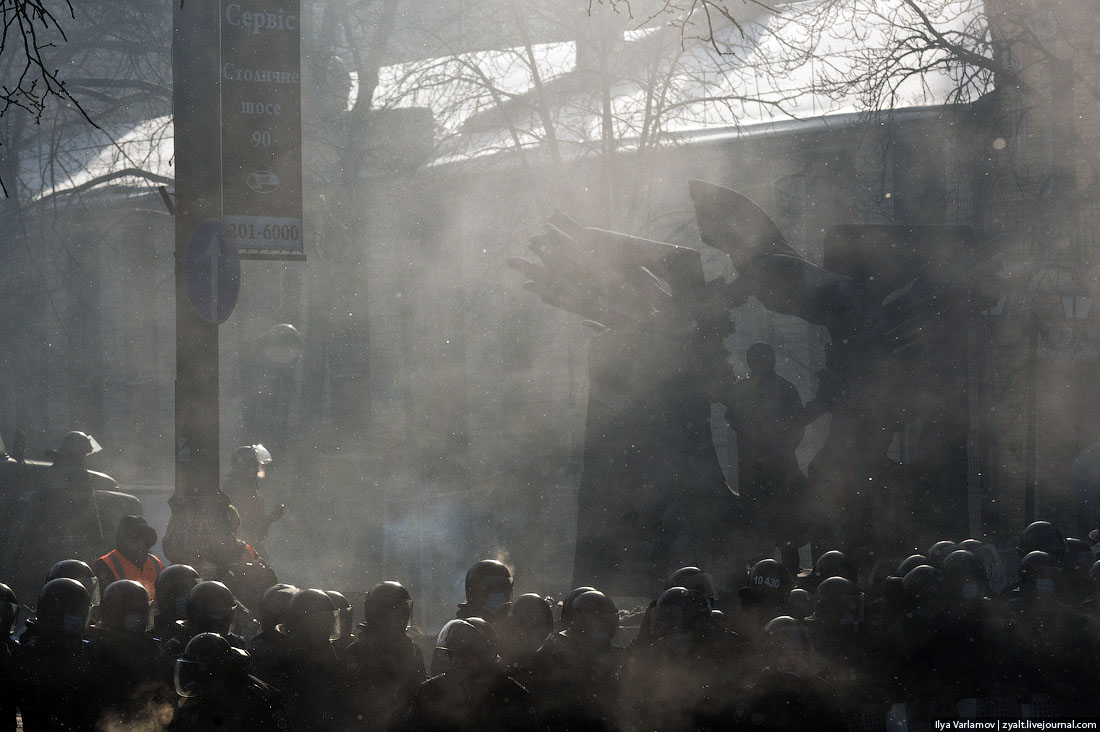
52. Monument to Lobanovsky next to the stadium is neatly covered with cloth.
53. People get warm next to campfire. Is revolution possible without a bicycle? I say no!
54. People on the hill are prepared for an assault. Stones, incendiary bottles and tires tightened with barbwire will be thrown to the attackers in case of necessity. 
55. “Katyusha rocket launchers” used for shooting fireworks to the police.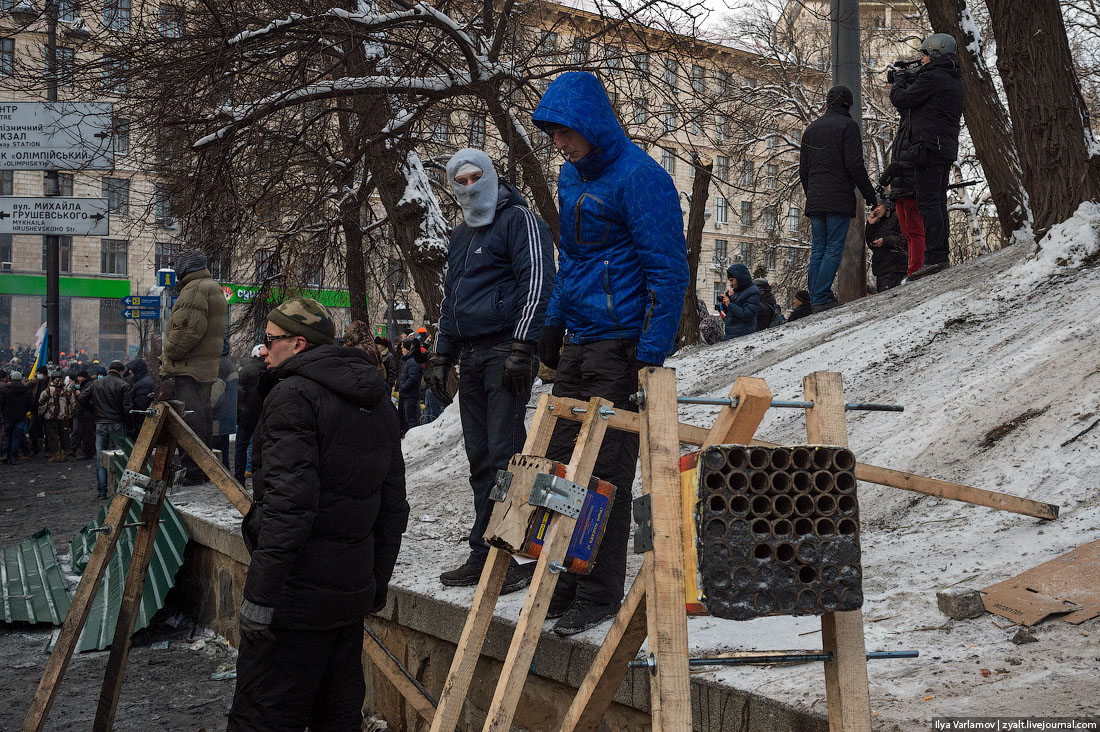
56. Preparation of Molotov’s cocktails.
57. Bottles and stones.
58. Cocktails are being prepared by women.
59. You’ve probably heard about people banging metal with sticks. Many asked why – this is sort of a signal. When nothing happens, nobody is taping. When casual stone- and grenade-throwing takes place, the knock is monotonous, in order to set rhythm and keep the morale. When Berkut attacks, drumming becomes louder and everyone hears that – for some it is a signal to run away, for some, on the opposite – defend the barricades.
60. Man glues his store’s showcase, even though not a single his window was broken in four days. This store sells expensive furniture, and the ad urges not to rob it. As I said, there are no marauders in Kyiv – everything is perfectly organized, contrary to Bishkek, where, as I remember, the city was plundered in half a day. Nothing like that takes place here.
61. People hammer the snow, then load it to sacks and bring to the barricades. Snow serves as the main building material here. Sacks are being poured by water and snow turns into ice – monolithic barricades which come out are very difficult to destroy.
62. The Maidan’s quarries. People break the sett into easy to throw stones, load into sacks and bring to the frontline.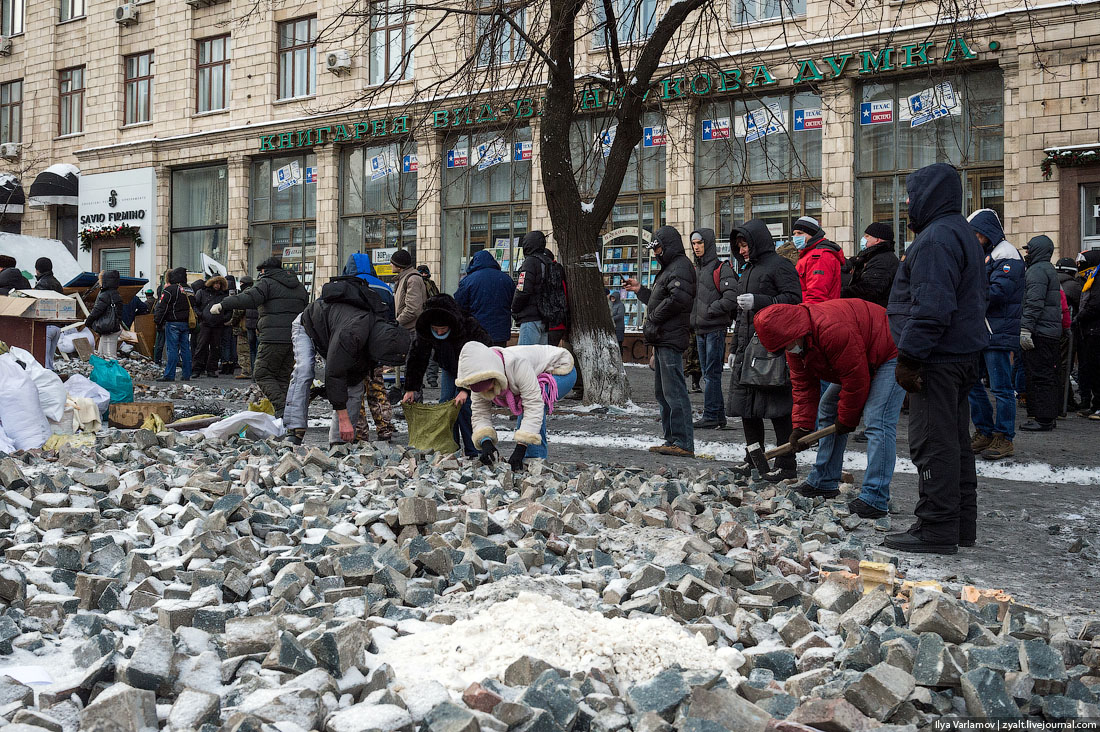
63. That’s how it looks.
64. They carry.
65. A stove.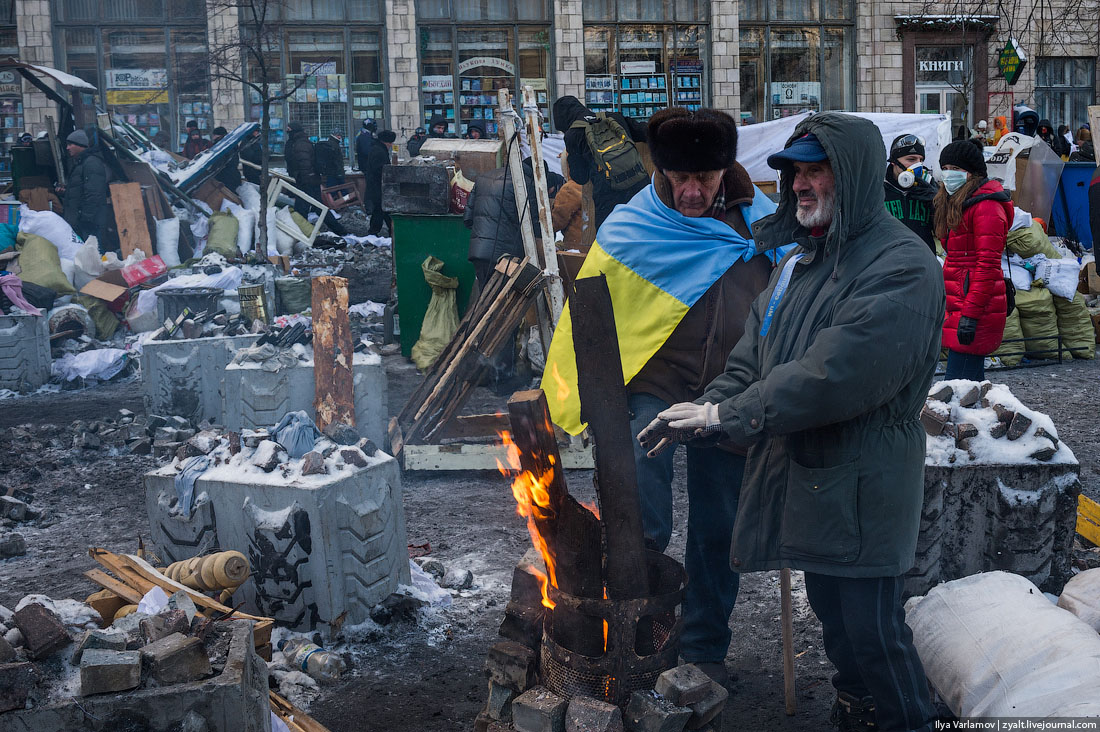
66. Modern art.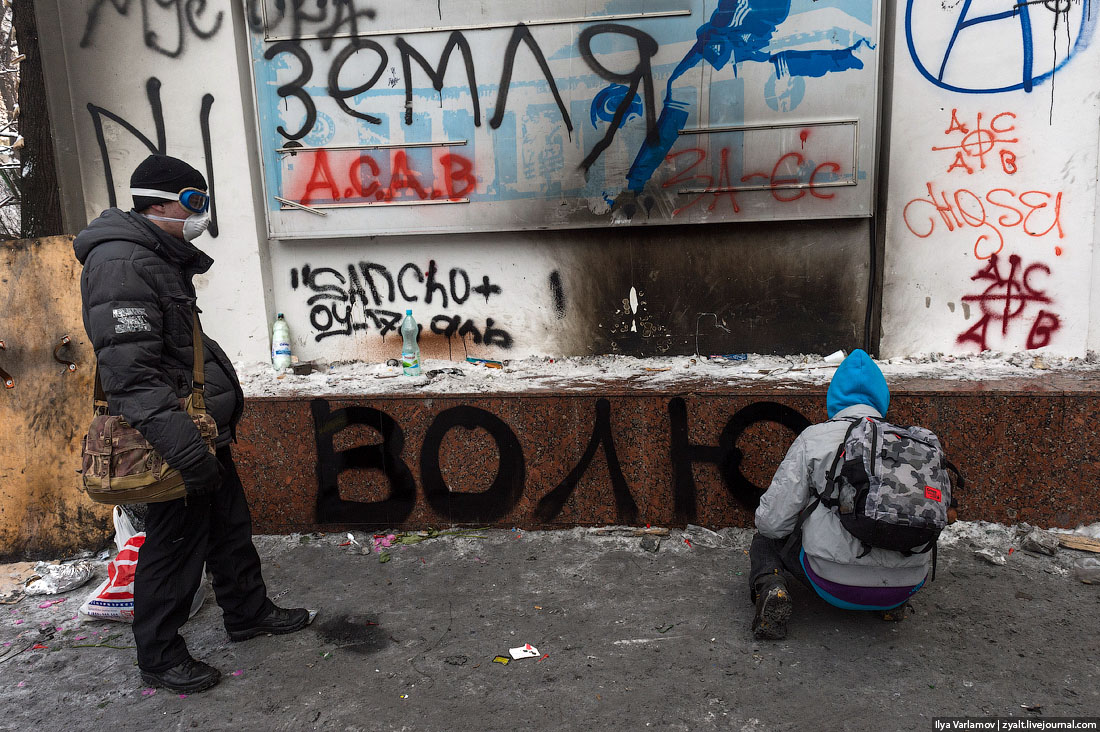
67. Someone started a rumor about the Armenian Diaspora willing to pay for any information about the murder of their compatriot on Maidan. Later it turned out to be fake. 
68. One of the protesters. Russian press usually describes the participants of Maidan as “extremists, radical thugs, ultras, members of nationalistic groups, motley nationalist, sometimes openly Nazist public, extremist militants, rioters, pogromists, rebels” etc…
69. A journalist.
70. According to NTV (russian pro-government tv-channel), this is an “amuck radical”.
71. Look at the people. I said it already, but will repeat: all social classes are present on the squares – from students to pensioners. 
72. Grannies for Timoshenko.
73. Another extremist.
74. Women with food and tea always walk among the protesters – sometimes it looks like you’re on a banquet, not on a revolution. To find someone hungry is an uneasy job: the man on photo complaints that he put on three kilograms in a month :). Food is being brought every day, usually it is supplied by sympathizing Kyevites and businessmen who can’t go to the barricades but support the revolution.
If you are a foreign journalist, feel free to reprint on your website or in your newspaper with reference or indication of authorship, and please let me know by sending the link to e-mail:kdguseva@gmail.com
Failed to delight — Founder Stories — Medium
Comments:"Failed to delight — Founder Stories — Medium"
URL:https://medium.com/founder-stories/4de7ef031c3a
We decided to flip the switch on Delight at the end of this month and it officially marks the end of my first startup. Bittersweet moment.
The vision of Delight was to build a new kind of mobile analytics: visual analytics. Traditional metrics tell you the what and we tell you the why by showing you the real interaction. We had some good initial response but we failed to take off. Here are some lessons we learned along the way.
Price for the values your service delivers.Our most expensive monthly plan was US$300. Customers who churned never complained about the price. We just didn’t deliver up to their expectation.Customers pay for information, not raw data.Again, it’s the value your service delivers. Customers are willing to pay a lot more for information and most are not interested in data. Your service should make your customers look intelligence to their stakeholders. It has always been on our roadmap to analyze the recordings so our users only need to watch the relevant ones. We never got to it though.Price your service to encourage engagement.We originally price by the number of recording credits. Since our customers had no control on the length of the recordings, most of them were very cautious on using up the credits. Plans based on the accumulated duration of recordings make much more sense for us and the number of subscription showed.Follow up with inactive users.This is especially true when your service does not give intermediate values to your users. In our case, our users would need to install our iOS SDK, distribute the apps and wait for actual usage before they could gain any insights from their recordings. Our system should have been smarter about checking upon our users at various stages.Welcome email works well.We got this idea from my YC batch mate Optimizely. Send an email to your new user and ask them about how they intend to use your service and where they heard about you. We got about 10% reply rate and gained insight on our target market and what pain points they wanted us to solve.Content marketing works well.Most of our traffic was from the mentions in other reputable blogs. These blogs have a long lasting effect. We continue to have new users from a blog post written well over a year.We didn’t pivot hard enough.Although Delight was born out of our own pain point when developing our second product, it was still nerve wracking telling the team the ship had to change course mid way. The company was founded on changing mobile video consumption and we ended up betting the company on building developer tools. Even though we saw promising signs early on, we waited too long to fully commit to it. The team was constantly distracted and didn’t know where the company was really heading.I’m extremely proud of the team and what we’ve achieved together. Although at the end our technical issues have stopped Delight from being used in a production environment, the ultimate reason on why we failed wasn’t the product nor the market.
It was me. I failed. I gave up.
It was my first startup and I was made a single founder a year after we started. I didn’t know how to handle the roller coaster ride and it took a toll on not only my physical and mental health but also my loved ones. So, I called it quits. More on that in Part 2.
The 100 Most Influential Books Ever Written by Martin Seymour-Smith - The Greatest Books
Comments:"The 100 Most Influential Books Ever Written by Martin Seymour-Smith - The Greatest Books"
URL:http://thegreatestbooks.org/lists/45
The 100 Most Influential Books Ever Written: The History of Thought from Ancient Times to Today (1998) is a book of intellectual history written by Martin Seymour-Smith (1928–1998), a British poet, critic, and biographer.
The story follows the life of one seemingly insignificant man, Winston Smith, a civil servant assigned the task of perpetuating the regime's propaganda by falsifying records and political literatur... - Wikipedia
I've read this book I want to read this book
The Aeneid is a Latin epic poem written by Virgil in the late 1st century BC (29–19 BC) that tells the legendary story of Aeneas, a Trojan who traveled to Italy, where he became the ancestor of the... - Wikipedia
I've read this book I want to read this book
I've read this book I want to read this book
Lunyu, also known as the Analects of Confucius, are considered a record of the words and acts of the central Chinese thinker and philosopher Confucius and his disciples, as well as the discussions ... - Wikipedia
I've read this book I want to read this book
An Essay Concerning Human Understanding is one of John Locke's two most famous works, the other being his Second Treatise on Civil Government. First appearing in 1690, the essay concerns the founda... - Wikipedia
I've read this book I want to read this book
The book An Essay on the Principle of Population was first published anonymously in 1798 through J. Johnson (London). The author was soon identified as The Reverend Thomas Robert Malthus. While it ... - Wikipedia
I've read this book I want to read this book
The Annals (Latin: Annales) is a history book by Tacitus covering the reign of the four Roman Emperors succeeding to Caesar Augustus. The parts of the work that survived from antiquity cover most o... - Wikipedia
I've read this book I want to read this book
The Avesta is the primary collection of sacred texts of Zoroastrianism, composed in the Avestan language. - Wikipedia
I've read this book I want to read this book
I've read this book I want to read this book
Being and Nothingness: An Essay on Phenomenological Ontology, sometimes subtitled A Phenomenological Essay on Ontology, is a 1943 philosophical treatise by Jean-Paul Sartre. Its main purpose was to... - Wikipedia
I've read this book I want to read this book
In Beyond Freedom and Dignity, Skinner suggests that a technology of behavior could help to make a better society. We would, however, have to accept that an autonomous agent is not the driving forc... - Wikipedia
I've read this book I want to read this book
Candide, ou l'Optimisme is a French satire written in 1759 by Voltaire, a philosopher of the Age of Enlightenment. Candide is characterized by its sarcastic tone and its erratic, fantastical, an... - Wikipedia
I've read this book I want to read this book
I've read this book I want to read this book
I've read this book I want to read this book
Manifesto of the Communist Party (German: Manifest der Kommunistischen Partei), often referred to as The Communist Manifesto, was published on February 21, 1848, and is one of the world's most infl... - Wikipedia
I've read this book I want to read this book
Confessions is the name of an autobiographical work, consisting of 13 books, by St. Augustine of Hippo, written between AD 397 and AD 398. Modern English translations of it are sometimes published ... - Wikipedia
I've read this book I want to read this book
Confessions is an autobiographical book by Jean-Jacques Rousseau. In modern times, it is often published with the title The Confessions of Jean-Jacques Rousseau in order to distinguish it from St. ... - Wikipedia
I've read this book I want to read this book
The Corpus Aristotelicum is the collection of Aristotle's works that have survived from antiquity through Medieval manuscript transmission. These texts, as opposed to Aristotle's lost works, are te... - Wikipedia
I've read this book I want to read this book
I've read this book I want to read this book
The Critique of Pure Reason (German: Kritik der reinen Vernunft ) by Immanuel Kant, first published in 1781, second edition 1787, is one of the most influential works in the history of philosophy. ... - Wikipedia
I've read this book I want to read this book
Cybernetics is the interdisciplinary study of the structure of regulatory systems. Cybernetics is closely related to control theory and systems theory. Both in its origins and in its evolution in t... - Wikipedia
I've read this book I want to read this book
The History of the Decline and Fall of the Roman Empire was written by English historian Edward Gibbon and published in six volumes. Volume I was published in 1776, and went through six printings. ... - Wikipedia
I've read this book I want to read this book
De rerum natura is a first century BC epic poem by the Roman poet and philosopher Lucretius with the goal of explaining Epicurean philosophy to a Roman audience. The poem, written in dactylic hexam... - Wikipedia
I've read this book I want to read this book
The Dhammapada is a versified Buddhist scripture traditionally ascribed to the Buddha himself. It is one of the best-known texts from the Theravada canon. - Wikipedia
I've read this book I want to read this book
The Dialogue Concerning the Two Chief World Systems was a 1632 Italian language book by Galileo Galilei comparing the Copernican system with the traditional Ptolemaic system. It was translated to L... - Wikipedia
I've read this book I want to read this book
Published on 15 April 1755 and written by Samuel Johnson, A Dictionary of the English Language, sometimes published as Johnson's Dictionary, is among the most influential dictionaries in the histor... - Wikipedia
I've read this book I want to read this book
I've read this book I want to read this book
Belonging in the immortal company of the great works of literature, Dante Alighieri's poetic masterpiece, The Divine Comedy, is a moving human drama, an unforgettable visionary journey through the ... - Publisher
I've read this book I want to read this book
Alonso Quixano, a retired country gentleman in his fifties, lives in an unnamed section of La Mancha with his niece and a housekeeper. He has become obsessed with books of chivalry, and believes th... - Wikipedia
I've read this book I want to read this book
Published in two volumes in 1843, Either/Or (original Danish title: Enten ‒ Eller) is an influential book written by the Danish philosopher Søren Kierkegaard, exploring the aesthetic and ethical "p... - Wikipedia
I've read this book I want to read this book
Encyclopédie, ou dictionnaire raisonné des sciences, des arts et des métiers (English: Encyclopedia, or a systematic dictionary of the sciences, arts, and crafts) was a general encyclopedia publish... - Wikipedia
I've read this book I want to read this book
The Six Enneads, sometimes abbreviated to The Enneads or Enneads (Greek: Ἐννεάδες), is the collection of writings of Plotinus, edited and compiled by his student Porphyry (c. 270 AD). Plotinus was ... - Wikipedia
I've read this book I want to read this book
William Godwin (3 March 1756 – 7 April 1836) was an English journalist, political philosopher and novelist. He is considered one of the first exponents of utilitarianism, and one of the first moder... - Wikipedia
I've read this book I want to read this book
Essays is the title given to a collection of 107 essays written by Michel de Montaigne that was first published in 1580. Montaigne essentially invented the literary form of essay, a short subjectiv... - Wikipedia
I've read this book I want to read this book
I've read this book I want to read this book
Euclid's Elements (Greek: Στοιχεῖα) is a mathematical and geometric treatise consisting of 13 books written by the Greek mathematician Euclid in Alexandria circa 300 BC. It is a collection of defin... - Wikipedia
I've read this book I want to read this book
Written in 1865 by Gregor Mendel, Experiments on Plant Hybridization (German: Versuche über Pflanzen-Hybriden) was the result after years spent studying genetic traits in pea plants. Mendel read hi... - Wikipedia
I've read this book I want to read this book
The Feminine Mystique, published 25 February 1963, is a book written by Betty Friedan which brought to light the lack of fulfillment in many women's lives, which was generally kept hidden[citation ... - Wikipedia
I've read this book I want to read this book
Mr. William Shakespeares Comedies, Histories, & Tragedies is the 1623 published collection of William Shakespeare's plays. Modern scholars commonly refer to it as the First Folio. Printed in folio... - Wikipedia
I've read this book I want to read this book
I've read this book I want to read this book
The Life of Gargantua and of Pantagruel (in French, La vie de Gargantua et de Pantagruel) is a connected series of five novels written in the 16th century by François Rabelais. It is the story of t... - Wikipedia
I've read this book I want to read this book
The General Theory of Employment, Interest and Money was written by the English economist John Maynard Keynes. The book, generally considered to be his magnum opus, is largely credited with creatin... - Wikipedia
I've read this book I want to read this book
The Gospel of Truth is one of the Gnostic texts from the New Testament apocrypha found in the Nag Hammadi codices ("NHC"). It exists in two Coptic translations, a Subachmimic rendition surviving al... - Wikipedia
I've read this book I want to read this book
The Guide for the Perplexed is one of the major works of Rabbi Moshe ben Maimon, better known as Maimonides or "the Rambam". It was written in the 12th century in the form of a three-volume letter ... - Wikipedia
I've read this book I want to read this book
Harmonices Mundi (Latin: The Harmony of the Worlds, 1619) is a book by Johannes Kepler. In the work Kepler discusses harmony and congruence in geometrical forms and physical phenomena. The final se... - Wikipedia
I've read this book I want to read this book
The Hebrew Bible is a term referring to the books of the Jewish Bible as originally written mostly in Biblical Hebrew with some Biblical Aramaic. The term closely corresponds to contents of the Jew... - Wikipedia
I've read this book I want to read this book
The Hippocratic Corpus, Hippocratic Collection, or Hippocratic Canon, is a collection of around seventy early medical works from ancient Greece strongly associated with the ancient Greek physician ... - Wikipedia
I've read this book I want to read this book
The Histories of Herodotus is considered one of the seminal works of history in Western literature. Written from the 450s to the 420s BC in the Ionic dialect of classical Greek, The Histories serve... - Wikipedia
I've read this book I want to read this book
The History of the Peloponnesian War is an account of the Peloponnesian War in Ancient Greece, fought between the Peloponnesian League (led by Sparta) and the Delian League (led by Athens). It was ... - Wikipedia
I've read this book I want to read this book
Ich und Du, usually translated as I and Thou, is a book by Martin Buber, published in 1923, and first translated to English in 1937. Buber's main proposition is that we may address existence in two... - Wikipedia
I've read this book I want to read this book
The I Ching, Classic of Changes or Book of Changes; also called Zhouyi, is one of the oldest of the Chinese classic texts. The book contains a divination system comparable to Western geomancy or th... - Wikipedia
I've read this book I want to read this book
The Iliad is an epic poem in dactylic hexameters, traditionally attributed to Homer. Set in the Trojan War, the ten-year siege of Ilium by a coalition of Greek states, it tells of the battles and e... - Wikipedia
I've read this book I want to read this book
Institutes of the Christian Religion (Institutio Christianae religionis) is John Calvin's seminal work on Protestant systematic theology. Highly influential in the Western world and still widely re... - Wikipedia
I've read this book I want to read this book
This book introduces Freud's theory of the unconscious with respect to dream interpretation. Dreams, in Freud's view, were all forms of "wish-fulfillment" — attempts by the unconscious to resolve a... - Wikipedia
I've read this book I want to read this book
Kabbalah is a discipline and school of thought concerned with the mystical aspect of Judaism. It is a set of esoteric teachings that is meant to explain the relationship between an infinite, eterna... - Wikipedia
I've read this book I want to read this book
Leviathan, The Matter, Forme and Power of a Common Wealth Ecclesiasticall and Civil, commonly called Leviathan, is a book written by Thomas Hobbes which was published in 1651. It is titled after th... - Wikipedia
I've read this book I want to read this book
Logik der Forschung is a 1934 book by Karl Popper. It was originally written in German, but reformulated in English by Popper himself some years later, to be published as The Logic of Scientific Di... - Wikipedia
I've read this book I want to read this book
Meditations (Τὰ εἰς ἑαυτόν, Ta eis heauton, literally "thoughts/writings addressed to himself") is the title of a series of personal writings by Marcus Aurelius setting forth his ideas on Stoic phi... - Wikipedia
I've read this book I want to read this book
The Mind and Society (1916) is the English title of the seminal sociological work Trattato di Sociologia Generale by the Italian sociologist and economist Vilfredo Pareto (1848-1923). - Wikipedia
I've read this book I want to read this book
I've read this book I want to read this book
The New Testament is the name given to the second major division of the Christian Bible, the first such division being the much longer Old Testament, both terms being associated with Supersessionis... - Wikipedia
I've read this book I want to read this book
The Novum Organum is a philosophical work by Francis Bacon published in 1620. The title translates as "new instrument". This is a reference to Aristotle's work Organon, which was his treatise on lo... - Wikipedia
I've read this book I want to read this book
The Odyssey is one of two major ancient Greek epic poems attributed to Homer. It is, in part, a sequel to the Iliad, the other work traditionally ascribed to Homer. The poem is fundamental to the m... - Wikipedia
I've read this book I want to read this book
On Liberty is a philosophical work by 19th century English philosopher John Stuart Mill, first published in 1859. To the Victorian readers of the time it was a radical work, advocating moral and ec... - Wikipedia
I've read this book I want to read this book
Although the term Babylonian captivity, or Babylonian exile, typically refers to the deportation and exile of the Jews of the ancient Kingdom of Judah to Babylon by Nebuchadnezzar II in 586 BC, in ... - Wikipedia
I've read this book I want to read this book
Charles Darwin's On the Origin of Species, published on Thursday 24 November 1859, is a seminal work of scientific literature considered to be the foundation of evolutionary biology. Its full title... - Wikipedia
I've read this book I want to read this book
De revolutionibus orbium coelestium (On the Revolutions of the Heavenly Spheres), first printed in 1543 in Nuremberg, is the seminal work on the heliocentric theory of astronomer Nicolaus Copernicu... - Wikipedia
I've read this book I want to read this book
Vom Kriege is a book on war and military strategy by Prussian general Carl von Clausewitz, written mostly after the Napoleonic wars, between 1816 and 1830, and published posthumously by his wife in... - Wikipedia
I've read this book I want to read this book
Philosophical skepticism (from Greek σκέψις - skepsis meaning "enquiry" - UK and traditional spelling, scepticism) is both a philosophical school of thought and a method that crosses disciplines an... - Wikipedia
I've read this book I want to read this book
Plutarch's Lives of the Noble Greeks and Romans, commonly called Parallel Lives or Plutarch's Lives, is a series of biographies of famous men, arranged in tandem to illuminate their common moral vi... - Wikipedia
I've read this book I want to read this book
I've read this book I want to read this book
I've read this book I want to read this book
Philosophical Investigations is, along with the Tractatus Logico-Philosophicus, one of the two most influential works by the 20th-century philosopher Ludwig Wittgenstein. In it, Wittgenstein discus... - Wikipedia
I've read this book I want to read this book
One of the most powerful dramas of Christian faith ever written, this captivating allegory of man's religious journey in search of salvation follows the pilgrim as he travels an obstacle-filled roa... - Publisher
I've read this book I want to read this book
I've read this book I want to read this book
The Praise of Folly (Greek title: Morias Enkomion (Μωρίας Εγκώμιον), Latin: Stultitiae Laus, sometimes translated as In Praise of Folly, Dutch title: Lof der Zotheid) is an essay written in 1509 by... - Wikipedia
I've read this book I want to read this book
Il Principe (The Prince) is a political treatise by the Florentine public servant and political theorist Niccolò Machiavelli. Originally called De Principatibus (About Principalities), it was origi... - Wikipedia
I've read this book I want to read this book
I've read this book I want to read this book
I've read this book I want to read this book
Quotations from Chairman Mao Zedong (simplified Chinese: 毛主席语录; pinyin: Máo zhǔxí yǔlù), better known in the West as The Little Red Book, was published by the Government of the People's Republic of... - Wikipedia
I've read this book I want to read this book
The Qur’an is the central religious text of Islam, also sometimes transliterated as Quran, Qur’ān, Koran, Alcoran or Al-Qur’ān. Muslims believe the Qur’an to be the book of divine guidance and dire... - Wikipedia
I've read this book I want to read this book
Reflections on the Revolution in France (1790), by Edmund Burke, is one of the best-known intellectual attacks against the (then-infant) French Revolution. In the twentieth century, it much influen... - Wikipedia
I've read this book I want to read this book
In clear, concise language that is accessible to all, Albert Einstein's brilliant theory is explained and its implications discussed. - Publisher
I've read this book I want to read this book
The Republic is a Socratic dialogue by Plato, written c. 380 B.C.E.. It is one of the most influential works of philosophy and political theory, and Plato's best known work. In Plato's fictional di... - Wikipedia
I've read this book I want to read this book
The Road to Serfdom is a book written by Friedrich von Hayek (recipient of the Nobel Memorial Prize in Economic Sciences in 1974) which transformed the landscape of political thought in the 20th ce... - Wikipedia
I've read this book I want to read this book
The Second Sex (French: Le Deuxième Sexe, June 1949) is one of the best-known works of the French existentialist Simone de Beauvoir. It is a work on the treatment of women throughout history and of... - Wikipedia
I've read this book I want to read this book
The Structure of Scientific Revolutions is an analysis of the history of science. Its publication was a landmark event in the sociology of knowledge, and popularized the terms paradigm and paradigm... - Wikipedia
I've read this book I want to read this book
The Summa Theologica (Latin: "Summary of Theology" or "Highest Theology") or the Summa Theologiæ or simply the Summa, written 1265–1274) is the most famous work of Thomas Aquinas (c. 1225–1274), al... - Wikipedia
I've read this book I want to read this book
Syntactic Structures is an influential book by American linguist Noam Chomsky, first published in 1957. Widely regarded as one of the most important texts in the field of linguistics, this work lai... - Wikipedia
I've read this book I want to read this book
The Tao Te Ching or Dao De Jing, originally known as Laozi, a record-keeper at the Zhou Dynasty court, by whose name the text is known in China. The text's true authorship and date of composition o... - Wikipedia
I've read this book I want to read this book
Thus Spoke Zarathustra: A Book for All and None (German: Also sprach Zarathustra: Ein Buch für Alle und Keinen) is a philosophical novel by German philosopher Friedrich Nietzsche, composed in four ... - Wikipedia
I've read this book I want to read this book
A Treatise Concerning the Principles of Human Knowledge (Commonly called "Treatise" when referring to Berkeley's works) is a 1710 work by Anglo-Irish Empiricist philosopher George Berkeley. This bo... - Wikipedia
I've read this book I want to read this book
A Treatise of Human Nature is a book by Scottish philosopher David Hume, first published in 1739–1740. - Wikipedia
I've read this book I want to read this book
I've read this book I want to read this book
Written in 1914, The Trial is one of the most important novels of the twentieth century: the terrifying tale of Josef K., a respectable bank officer who is suddenly and inexplicably arrested and mu... - Publisher
I've read this book I want to read this book
The Upanishads are Hindu scriptures that constitute the core teachings of Vedanta.[1] They do not belong to any particular period of Sanskrit literature: the oldest, such as the Brhadaranyaka and C... - Wikipedia
I've read this book I want to read this book
A Vindication of the Rights of Woman: with Strictures on Political and Moral Subjects (1792), written by the eighteenth-century British feminist Mary Wollstonecraft, is one of the earliest works of... - Wikipedia
I've read this book I want to read this book
Epic in scale, War and Peace delineates in graphic detail events leading up to Napoleon's invasion of Russia, and the impact of the Napoleonic era on Tsarist society, as seen through the eyes of fi... - Wikipedia
I've read this book I want to read this book
An Inquiry into the Nature and Causes of the Wealth of Nations (generally referred to by the short title The Wealth of Nations) is the magnum opus written by Scottish economist and moral philosophe... - Wikipedia
I've read this book I want to read this book
Gottfried Wilhelm von Leibniz (German pronunciation: [ˈgɔtfrit ˈvɪlhɛlm fən ˈlaɪpnɪts]; 1 July 1646 [OS: 21 June] – 14 November 1716) was a German philosopher, polymath and mathematician who wrote ... - Wikipedia
I've read this book I want to read this book
The World as Will and Representation (Die Welt als Wille und Vorstellung) is the central work of German philosopher Arthur Schopenhauer. It was published in December 1818. - Wikipedia
I've read this book I want to read this book
3 Enemas Later, Still No Drugs
Mac Pro (late 2013) replica
Comments:" Mac Pro (late 2013) replica"
URL:http://www.tonymacx86.com/mac-pro-mods/120757-mac-pro-late-2013-replica.html
Mac Pro (late 2013) replica
Edit (15th of january 2014):
As this build gets so much attention I think I have to clarify some details.
I am NOT the builder of this mod. I got the permission of the "modder" to present the mod here. The original thread of the build has been in a german forum, which name I am not allowed to post, and has already been deleted. The admins of the source forum are a little restictive....
All credit goes to the user "sascha288", he is the owner and builder of that case.
Because I have been threatened to get sued by the german forum admins, I had to remove the link to the original post. I'm not a professional in internet law/rights and just wanted to help.
-----------
I am writting on behalf of a user from a german Forum (had to delete the link… o_O )
The mod/case is based on (yes) a trashcan: Authentics - Lunar http://www.amazon.de/Authentics-1200...entics+-+Lunar
Dimensions: 18cm width, 26cm height
Costs for the marterial (no PC hardware): 60€
Hardware:
Core i3 (Haswell)
Gigabyte z87n wifi
Radeon 7750
SDD & HDD
ATX PSU
Back:

Bottom fan:
Mainboard mounting:




New back:
Top view:
Core parts mounted + additional top fan:

working on the back:

painting case red:
hand crafted bottom intake:




almost finished:




Idle temperatures:
Hope you like it ![]()
Inception | Break & Enter
Comments:" Inception | Break & Enter "
URL:http://www.breaknenter.org/projects/inception/
Inception is a FireWire physical memory manipulation and hacking tool exploiting IEEE 1394 SBP-2 DMA. The tool can unlock (any password accepted) and escalate privileges to Administrator/root on almost* any powered on machine you have physical access to. The tool can attack over FireWire, Thunderbolt, ExpressCard, PC Card and any other PCI/PCIe interfaces.
Inception aims to provide a stable and easy way of performing intrusive and non-intrusive memory hacks on live computers using FireWire SBP-2DMA. It is primarily intended to do its magic against computers that utilize full disk encryption such as BitLocker, FileVault, TrueCrypt or Pointsec. There are plenty of other ways to hack a machine that doesn’t pack encryption. Inception is also useful for incident response teams and digital forensics experts when faced with live machines.
Inception’s main mode works as follows: By presenting a Serial Bus Protocol 2 (SBP-2) unit directory to the victim machine over the IEEE1394 FireWire interface, the victim operating system thinks that a SBP-2 device has connected to the FireWire port. Since SBP-2 devices utilize Direct Memory Access (DMA) for fast, large bulk data transfers (e.g., FireWire hard drives and digital camcorders), the victim lowers its shields and enables DMA for the device. The tool now has full read/write access to the lower 4GB of RAM on the victim. Once DMA is granted, the tool proceeds to search through available memory pages for signatures at certain offsets in the operating system’s password authentication modules. Once found, the tool short circuits the code that is triggered if an incorrect password is entered.
An analogy for this operation is planting an idea into the memory of the machine; the idea that every password is correct. In other words, the nerdy equivalent of a memory inception.
After running the tool you should be able to log into the victim machine using any password.
The in-memory patching is non-persistent, and a reboot will restore the normal password functionality. This contributes to a key property of Inception: It’s stealthy.
You can also use Inception to elevate privileges on (almost) any machine you have physical access to. As the tool patches the inner authentication mechanism in the OS, you can elevate your privileges to Local Adminstrator / root by using the Windows runas or Linux/OS X sudo su -s commands.
As of version 0.3.1, it is able to unlock Windows 8.0-1, Windows 7 SP0-1, Vista SP0 and SP2, Windows XP SP2-3, Mac OS X Mavericks, Snow Leopard, Lion and Mountain Lion, Ubuntu 11.04, 11.10, 12.04, 12.10, 13.04, Linux Mint 11, 12 and 13 x86 and x64-bit machines. Signatures are added by request.
Inception requires:
- A unix-flavor operating system to perform the attack from:
- Linux with the ‘Juju’ IEEE FireWire stack (Ubuntu 11 and higher and BackTrack 5 is known to work)
- Mac OS X (via IOkit, not recommended as IOkit is notoriously buggy at the moment)
- Python 3 (http://www.python.org)
- libforensic1394 (https://freddie.witherden.org/tools/libforensic1394/)
- A FireWire/Thunderbolt/ExpressCard/PC Card interface at both machines. If you don’t have a native FireWire port, you can buy an adapter to hotplug one. The tool works over anything that expands the PCIe bus
The latest development version can always be fetched from GitHub.
You should be able to run the tool without any installation (except the dependencies) on Mac OS X and Linux operating systems. Please be referred to the README file in libforensic1394 for installation of the libraries and FireWire pro-tips.
Dependencies
On Debian-based distros the process of installing the dependencies and the tool may be summarized as the following commands:
sudo apt-get install git cmake python3 g++ wget http://freddie.witherden.org/tools/libforensic1394/releases/libforensic1394-0.2.tar.gz tar xvf libforensic1394-0.2.tar.gz cd libforensic1394-0.2 cmake CMakeLists.txt sudo make install cd python sudo python3 setup.py install
The tool
Unzip the tool into a suitable directory, or fetch the latest development version from GitHub:
git clone https://github.com/carmaa/inception.git cd inception
To install the attack script natively, use the supplied setup.py script (as root if required by your OS):
sudo ./setup.py install
Please test Inception on a similar target before running it against a production box. A full list of available functionality of the tool can is available by running the tool with the -h/–help switch:
./incept --help
General usage
To run, hook up your host computer to a target using available FireWire interfaces or expansion ports and simply type (as root if required by your OS):
incept
The tool automatically loads signatures from the configuration file, and you can specify your own if you want to using the -s switch or by editing the file. The file contains a syntax defining search signatures, patches and offsets.
Memory dumping
To dump memory off the target machine to a file at the host, use the -D/-d/–dump switches. -D dumps all available memory, while -d dumps a specific region as specified by the user. Memory content is dumped to files with the file name syntax: ‘memdump_START-END.bin’. Examples:
Dumping 5 MiB of memory from offset 0xffff:
incept -d 0xffff,5MiB

Dumping all memory (up to 4 GiB):
incept -D
Pickpocket mode
To automatically dump memory from target machines that connects to a FireWire or Thunderbolt Daisy chain where your attacking machine is connected, use the -p/–pickpocket switch:
incept --pickpocket
Not working you say? Here’s a couple of hints:
- First, use the -v switch to visually confirm that the tool is able to read memory from the victim.
- Make sure you actually are connected with a IEEE134 FireWire cable (FireWire to USB converters, etc. won’t work, but 4/6/9 pin FireWire adapters do). Doh.
- “No firewire devices detected on the bus”
- First, try running the tool again.
- If you get this error message, try a different cable and/or using a couple of converters (such as this and this) to convert from 6/9 pin FireWire connector to 4 pin and back again. 6/9 pin FireWire cables are capable of transferring power, and this may cause trouble for some FireWire chipsets. Some FireWire cables are also known to be “straight-through” (i.e., not “crossover”), an this is known to cause trouble.
- Are you attacking from an OS that doesn’t support hot-plugging (such as BackTrack) using a ExpressCard/etc. on the host side? Re-boot the machine with the expansion card plugged in before running Inception.
- Are you sure you’re getting DMA? Sometimes the target machine uses an extended period of time (I’ve experienced time-spans up to around 30 secs on slow targets) installing the FireWire drivers and lowering the DMA shield; it is possible that you just didn’t wait long enough before attacking. Use the delay switch to increase the delay, and -v/–verbose to see if you actually read data. Also, looking in the Device Manager (assuming you are setting up a demo attacking Windows) may be helpful to see that a FireWire SBP2 device actually pops up when running the tool. Mind you, it is all right with a yellow exclamation mark by the device, the tool should work nevertheless.
- Does your target use some form of endpoint protection? Some antivirus vendors specifically block FireWire DMA. Turn it off and see what happens.
- Does your FireWire port work? Try connecting a FireWire disk and see if it is recognized. Check your BIOS setting to see that it is not disabled. Ensure that FireWire drivers are present and not removed from the system.
- Are you getting data, but still can’t find the signature? Check the above and see the FAQ below. Also check the amount of RAM installed (FireWire max addressable memory space is 4 GiB). The code may lie above that threshold, in which case the unlock attack won’t work. This is especially true for Linux machines, where kernel code resides in high memory addresses.
- Did Inception patch successfully, but you cannot log in? Try a non-blank password. Some OS authentication mechanisms check for blank passwords before passing control to the mechanism that Inception patches.
- Try again. Sometimes the DMA shield fails to lower on the first try/tries.
- Due to severe bugs in the Mac OS X FireWire stack IOKit, attacking from a Mac can cause a kernel panic at the target and/or host system if an error condition should occur. As of March 2012, attacking from Mac OS X is not recommended.
- Inception may not work reliably against machines with more than 4 GiB RAM, as the signatures the tool look for may be loaded at a memory address >
0xffffffff. You may still be able to exploit the target by dumping as much memory as possible and, say, search for encryption keys. - You may have trouble reading above 2 GiB on targets with more than 2 GiB RAM. This is due to the way the memory controller provisions physical addresses. Since there’s currently no way of detecting (over FireWire) how much physical memory the target has, the tool will continue to attempt to read memory up to the 4 GiB limit. You will see a noticeable slowdown in reading when the tool tries to read data from addresses that doesn’t map to hardware RAM.
- OS X Lion disables DMA when the user is logged out/screen is locked and FileVault is enabled. Attacking will only work while the user is logged in, or if user switching is enabled. The user switching trick only works for versions before 10.7.2, where the vulnerability is patched.
- If you have a OF/EFI firmware password set on the target Mac OS X, FireWire DMA is off by default.
To stay safe and protect against FireWire DMA attacks, here’s a couple of suggestions:
Windows
OS X
- Don’t panic – if you are using FileVault2 and OS X Lion (10.7.2) and higher, the OS will automatically turn off DMA when locked – you’re still vulnerable to attacks when unlocked, though
- Set a firmware password
Linux
All of the above will impact FireWire in one way or the other. Unfortunately, this is a FireWire design problem, not an OS problem, and would have to be fixed in the SBP-2 protocol itself.
Inception was originally coded as a GPL replacement for winlockpwn, the Windows FireWire unlock tool made available by Adam Bolieu aka Metlstorm. winlockpwn was quite stable against older Windows XP targets, but did not perform well against more modern operating system like Windows 7 (and it is not maintained anymore). As of Linux kernel 2.6.22 Linux Distros ships with the new ‘Juju’ FireWire stack, making winlockpwn obsolete. Alas, Inception was born.
DMA attacks has been known for many years, so this is nothing new (except for the fact that I will reverse engineer new signatures and update the tool’s functionality until the problem is fixed). However, vendors generally dismiss DMA attacks as a non-issue, which I hope that the awareness that this tool generates will change. Users deserve secure devices, even when attackers gain physical access.
- Your host OS
- The target OS (For Windows, the output of running winver.exe on the machine, format: major.minor.build, for Linux the output of uname -a and perhaps cat /etc/lsb-release)
- The target CPU architecture (x86/x64, etc.)
- Output of the tool
- Memory size of target
The tool makes use of the libforensic1394 library courtesy of Freddie Witherden under a LGPL license.
If you like tool, and especially if you use it successfully in a digital investigation, please consider making a donation to me using either option below.
My Bitcoin address
1ENpY2UTa8fB3nZpc1imZz1vj8zKHcNsxb
My PayPal account
The Letter-Heads
Christ, I hate Blackboard - Lawyers, Guns & Money : Lawyers, Guns & Money
Comments:" Christ, I hate Blackboard - Lawyers, Guns & Money : Lawyers, Guns & Money"
URL:http://www.lawyersgunsmoneyblog.com/2014/01/christ-i-hate-blackboard
Hundreds of years from now, after disease and fire and famine have thinned the human herd to a shrunken patchwork of sagging, skeletal bands of jagged, half-mad wraiths — when the parched soil chokes forth desiccated roots and the air is a toxic brume slumping down on the arched, knotted backs of the still-barely-living — a remote spur of humanity will somehow recover the capacity to speak, an ability long since abandoned by their ancestors, who were mute-struck with the unfathomable despair of those cursed to watch everything they love die. After generations of dry-throated croaking and lung-starched wheezing, their tongues swollen with thirst and punctured with abscesses that never heal, these distant people will bring forth a new language to survey the boundaries of their pain.
At first, their speech will flow together in single, blasphemous strands of adjectival protest; they will speak without subjects, no proper names or pronouns to jolt them into the kind of self-recognition that could only serve as a spur to mass, urgent suicide. In time, their words will be hacked into tinier fragments of salivated fury, as their lips and tongues and few-remaining-teeth jostle ruthlessly to disgorge themselves into the foul space that separates one antagonist from another. With arm-sized splinters of trees that were fortunate enough to perish centuries before, they will jab massive holes into their upper palates to accommodate the new sounds needed to register their misfortune and threaten each other with gross physical harm. Inbred mutants with hideous nasocranial deformities will gain selective advantage in the linguistic struggle for existence. They will use this new language to enslave one another, to plot out gristly sprees that might be called murder if there were anything near to law restraining them, like a weak sphincter, from unleashing their worst. There will be decades of forced labor, violent spasms of resistance and recrimination carried out with grossly disproportionate injury to bystanders who are, alas, never as innocent as they seem.
On the outskirts of this new language, lurking on its crimsoned frontier, will lie words that will themselves have been cast into exile – foul offgassings within a lexicon that itself stands as a towering monument to the boundlessly obscene, words that will curve backward and devour themselves, each one an afflicted universe in the process of total collapse, words that exist for microseconds before streaking, unremembered and unmourned, into the void.
These are the words, if I could shit them into being, that I would use to catalogue the depth of my loathing for Blackboard. When I die, I want my whiskey-pickled body larded into a cryonic chamber, then buried deep in the earth. A thousand years from now, I want these loping, crookspined human gargoyles to dig me up and reanimate me. I will learn their language; I will amble to the profane horizon of their blood-gorged vernacular; I will force them at spear-point to build me a time machine; then I will murder them all with my bare hands. I will return to all of you then to bear witness, in a rapturous tornado of filth, to my contempt for that unholy system of course mismanagement software.
Backer - A Crowdfunding Service from App.net
What I Wish I Had Known Before Selling to Google | Inc.com
Comments:"What I Wish I Had Known Before Selling to Google | Inc.com"
URL:http://www.inc.com/magazine/201402/jonathan-sposato/lessons-from-selling-to-google.html
Jonathan Sposato: Founder of Phatbits and Picnik
I founded Phatbits, which made XML desktop applications, in 2004. A year later, Google offered to acquire the business. We closed the deal after quick and collegial negotiations, and our group integrated into the Google Gadgets division easily.
My one regret was agreeing to stay on for four years. I wound up leaving after a year. I underestimated what it would feel like to be a salaryman, no longer in control of my own destiny. But overall, the integration was a success.
When I sold Picnik, a photo-sharing site, to Google five years later, I assumed everything would be about the same. That wasn't the case. This time, negotiations were complex, lasting almost six months.We faced a dizzying amount of changes in the first three months after the acquisition, being shuttled from one part of the company to the next.
One-third of our 25-person team, including my two business partners, quit right off the bat. I stayed for two years to offer some sense of continuity. By 2012, Google shut down Picnik entirely. I felt like I let a bunch of great people down.
Looking back, I should have insisted that Google's crystal ball for Picnik was clearer. I sometimes wonder whether I should have sold the company at all.
Now, as an angel investor in six startups, I advise entrepreneurs who are thinking about selling to think carefully about the return on investment, including the effect on team culture, not just the bottom line.
From the February 2014 issue of Inc. magazine
VOGONS • View topic - Emscripten port, for running in web browsers
Comments:"VOGONS • View topic - Emscripten port, for running in web browsers"
URL:http://www.vogons.org/viewtopic.php?f=32&t=38086
I wouldn't call it complete, but it runs many games well in Firefox. Chrome's JavaScript interpreter runs asm.js more slowly, but it can still run many real mode games with only minor sound glitches. Here are some demos:
The port also includes a Python script which transforms the CPU cores, using an array of function pointers instead of the main switch statement, with cases transformed into functions. This runs a lot faster in Chrome, because it can't optimize large switch statements. It even seems to run a bit faster in Firefox.
More information is available in README.md on GitHub.
April Fool Pranks in Sun Microsystems Over the Years
BeWifi lets you steal your neighbor’s bandwidth when they’re not using it | Ars Technica
Comments:"BeWifi lets you steal your neighbor’s bandwidth when they’re not using it | Ars Technica"
What if, when you were up at a ridiculous hour Skyping your relatives in Australia, you could borrow unused bandwidth from your sleeping neighbors to make your own broadband connection faster and stronger?
High up in a glass tower in Barcelona, Telefonica's research and development team has been attempting to tackle exactly this question. The solution they have come up with, BeWifi, is a technology that gathers bandwidth from local Wi-Fi routers in order to enhance the connection of the users that happen to be on the Internet at exactly that moment in time.
Telefonica started to research the idea, without making changes to existing infrastructure, in 2008. "We were exploring what would be the opportunities for bringing the peer-to-peer and sharing phenomenon into this arena," Pablo Rodriguez, Telefonica's Director of Product Innovation and Research, told Wired.co.uk.
"Your broadband connection is not used 100 percent of the time," he explained. "If you bring [connections] together smartly and manage to aggregate the spare capacity...[it's] a much better customer experience."
The way Telefonica has made this happen in a practical way is to build its own routers that can be installed in houses within a neighborhood. So far these have had to be installed by engineers, but the next generation are plug-and-play, and eventually all that will be needed is an over-the-air software update to customers' existing routers. According to Rodriguez, the software "creates a mesh to aggregate the capabilities [of the routers]." Pooling all of the bandwidth from these routers allows anyone within the network to take advantage of it at home, and they can also connect to any BeWifi network they come across on their mobile devices when out and about.
"From a technical point of view it's not trivial because you have to develop the software that is on the router to make sure that the router not only communicates with itself but also communicates in a mesh way with the other routers that are in the neighborhood," says Rodriguez.
The technology's only limitation is the actual Wi-Fi bandwidth available, he says. "What you need is some densely populated area—it could either be a small village or it could be a high-rise building, but you need to have some sort of community that is able to share the bandwidth."
Rodriguez is keen to emphasize that security has been a priority from the beginning and the network is completely safe and private. Homeowners will also always get priority over their own bandwidth, he says. "You always get at least what you paid for, but potentially you're going to get a lot more."
He does concede though that Telefonica needs to work out a way to deal with customers within a single network that are perhaps on different tariffs and are contributing more to the mesh than others. He suggests a system whereby the bandwidth a customer gets is somehow proportional to the capacity they bring into the system. This hasn't been a problem so far because the BeWifi pilots Telefonica has run so far in Catalonia have all involved households on the same tariff. By testing the technology in the market early on, Telefonica now has a better understanding of potential customer adoption and how it might scale the project further, Rodriguez explained.
When Telefonica advertised the first trial, over 1,000 people signed up in the north of Barcelona during the first week. "We were able to double the speed that customers were getting and we had some very interesting feedback," said Rodriguez, detailing that some people couldn't run Skype and YouTube at the same time before using BeWifi.
Through the pilot, Telefonica discovered that BeWifi also offered some unplanned benefits. One case involved a customer whose home broadband was suffering an outage. "His Internet connection came down and he was going through another Wi-Fi router from a nearby home and he didn't even notice it was happening," Rodriguez explains.
Another unexpected finding was that people do not use the Internet heavily all at exactly the same time—a concern at the beginning of the trial—but in sporadic bursts. This means there is nearly always some spare bandwidth available to be recycled.
Telefonica is currently looking towards developing economies and its huge customer base of over 200 million households in 14 countries in South America as the places in which BeWifi could have a real impact.
"Where it provides the most benefit is in areas where the connectivity [is poor]," says Rodriguez. "Where you need to do more with less, that's where technology helps you."
How Do I Cope with "Idea Overflow"?
Comments:"How Do I Cope with "Idea Overflow"?"
URL:http://lifehacker.com/how-do-i-cope-with-idea-overflow-1508415107
 SWrite down your ideas, forget about them, and put your nose to the grindstone. It's possible to stifle an overactive mind. The personal productivity experts at Stack Exchange offer tips on getting stuff done.
SWrite down your ideas, forget about them, and put your nose to the grindstone. It's possible to stifle an overactive mind. The personal productivity experts at Stack Exchange offer tips on getting stuff done.
How do I cope with "idea overflow"? My constant stream of new ideas is preventing me from realizing old ones. Specifically, I recently started two big projects. I started from scratch and had to learn a lot to be able to realize them. The problem is, the more I learn, the more new ideas I get and, and the harder it becomes to focus.
It's not just a question of distraction. Sometimes the new ideas improve the old ones. But then before I realize an improvement, a new idea comes to mind.I've tried the "Lean Method," but the problem is that implementation is always too slow. New ideas arise and slow the progress of my project. I've also tried not to start on anything new before finishing old tasks. This, too, hasn't worked.
Any suggestions on how to cope with this "idea overflow"?
See the original question here.
Agile methodologies (such as Scrum) recognize that we cannot know what will happen in the future, and accomodate for this fact by allowing users to periodically review their backlog of things to do. Whenever you come up with a new idea—great, add it to your backlog. Then pick it up for implementation at the next review if you think it's an idea that's good enough. That means something else may have to go.
Generally, you should never select a task and stick to it indefinitely, because the world and your insights change rapidly. Having many ideas is essentially a good thing, provided you record them in your backlog and don't let them overwhelm you by keeping them in your mind.
If you believe that you've found something much better to work with, regard the job you've already done on an obsolete task as a sunk cost. The key thing is to try to assess the net present value of each option, and go for the highest one.
As Gruber said in his answer, Agile methodologies will suite well for you. If you decide to adopt Scrum for yourself, the key thing to remember is that no planning should be done during an iteration. This means that at the beginning of an iteration you'll plan what you'll be doing for the next two or thre weeks (the iteration length can be adjusted to your needs, but usually 2-3 weeks works best), and then you shouldn't change any of your tasks, which includes not implementing anything new that wasn't planned beforehand.
Once an idea comes to you, write it down somewhere and try to forget about it. The idea might seem brilliant at the moment (or at least better than your current task), but it might not seem so good some time later. Give your ideas time to settle, then come back to them and try to assess them again with a fresh look (probably at the beginning of an iteration when you need to plan the next few weeks).
From my own experience, I worked in a small software company which suffered a lot because of such "idea overflow." We had new tasks before we had completed the previous ones, so eventually nothing was getting done. We had a bunch of incomplete stuff that wasn't working properly. But after we adopted Scrum and followed the key rule (which in our case was the same as I recommend to you: don't change the plans during an iteration), the situation improved significantly and we were surprised at how much we managed to accomplish.
And one more thing that I think could be helpful. Always assume that your new idea is a bad one. Don't rush to implement it, take your time. This combined with Scrum could really work for you.
Your mind is a great place to have ideas, not to store them (as said by David Allen, author of Getting Things Done). I suggest you write those ideas down in a place you trust. And then move on. Build into your routine a time to review those ideas (weekly? monthly? quarterly?). A trusting place can be a notebook, a private blog, a computer. It is better to stick to fewer places and simple tools.
The faster an idea is out, the faster you can resume what you were doing before the interruption. Putting ideas in writing will also give you the opportunity to take some distance, to "sleep on it." You will maybe discover relation between ideas, uncover patterns, and build specific expertise.
Disagree with the answers above? Have your own expertise to contribute? Check out the original question, and see more questions like this at Personal Productivity Stack Exchange, a question and answer site for people who want to improve their personal productivity. If you've got your own productivity problem that requires a solution, ask a question. You'll get an answer. (And it's free.)





